I have and will always love the challenge of defining cyber security architecture as a practice, process, lifestyle or what about system security architecture.. you know where I am going. So, there is no “cover it all” definition in my mind, as at least an enterprise security architecture is enterprise dependant and must be – it shall be business driven and therefore not globally defined. However, there are a lot of resources that help to define this.
Being SABSA certified, I cherish how SABSA is in my mind all about the “method”. Of what, why, how, who, where and when, with a multilayered approach; contextual, conceptual, logical, physical, component and management. Remember in all domains, People, Process and Technology (PPT). It aims to serve completeness, but as a method, it can and must be “eaten in protions”.
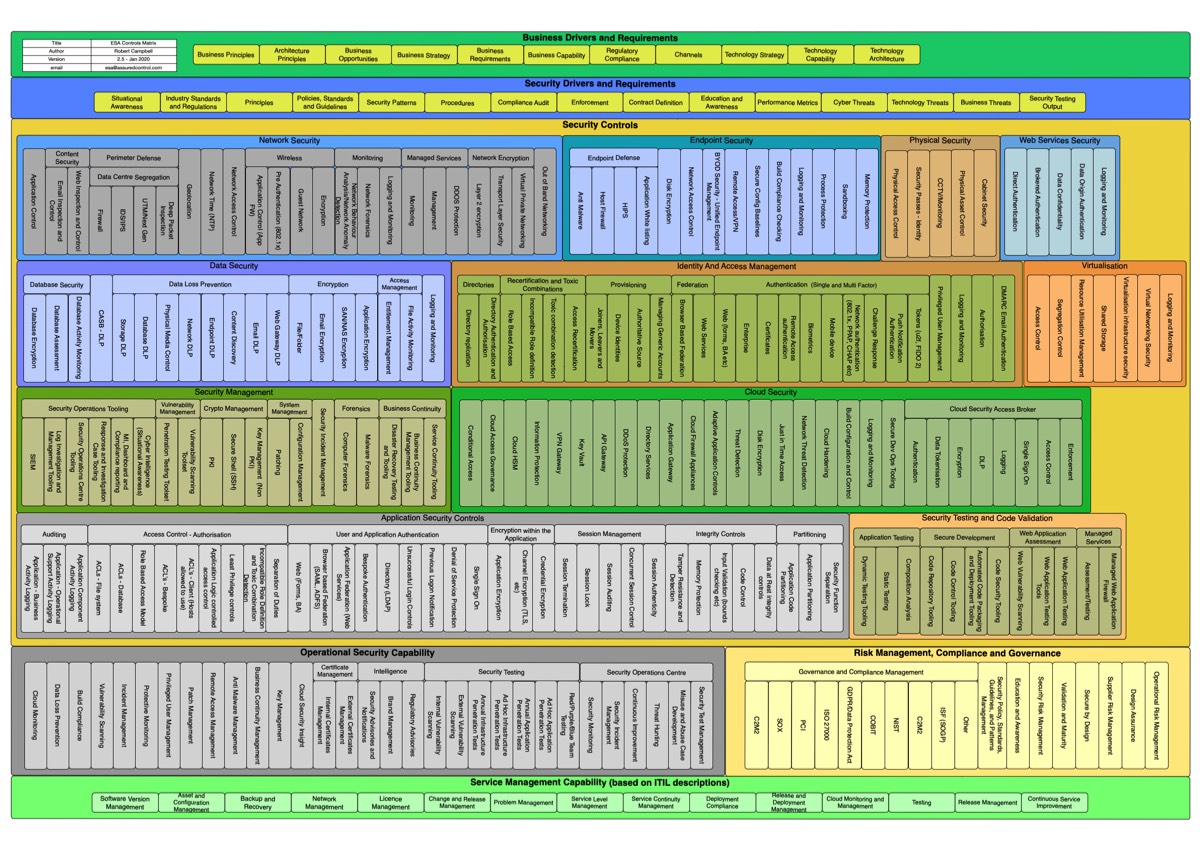
Even so, it nice to have examples and control matrises. Assuredcontrol have made a nice Security Controls Matrix for enterprise security architecture. It is quite heavy and may not cover it all, but it sure is a great cheat sheet.
Critical Security Controls, combined with the hardening guidelines is another worth mentioning. More threat driven, aimed at core/baseline controls however.
TOGAF also fits well with its aim at the enterprise security architecture practise. Along with ISACAs take on Enterprise Security Architecture—A Top-down Approach.
Security Reference Architecture
Zero-Trust (even how bad I think it has been commercialized) has a lot to bring to the table, and NIST does a good job defining it, to be aligned with the rest of the security architecture practise of course. And so is defined by Microsoft, and Googles Beyondcorp (with the original idea?) etc. Not to mention the service suppliers whitepapers, guidelines and blueprints, e.g., Googles Cloud Architecture Center, and Microsofts Cyber Reference Architectur, and AWS Cyber security reference architecture. In this regards, it is relevant also to mention CISAs vendor independent Cloud Security Reference Architecture.
This was not meant to be a complete guide or anywhere like it, but as the SA practise itself, it may be a lead.
