May be basic for most cyber Security professionals, but still, several of these cyber documentaries are worth watching while commuting to work or when flying!
Enterprise Security Architecture To-Be
I have and will always love the challenge of defining cyber security architecture as a practice, process, lifestyle or what about system security architecture.. you know where I am going. So, there is no “cover it all” definition in my mind, as at least an enterprise security architecture is enterprise dependant and must be – it shall be business driven and therefore not globally defined. However, there are a lot of resources that help to define this.
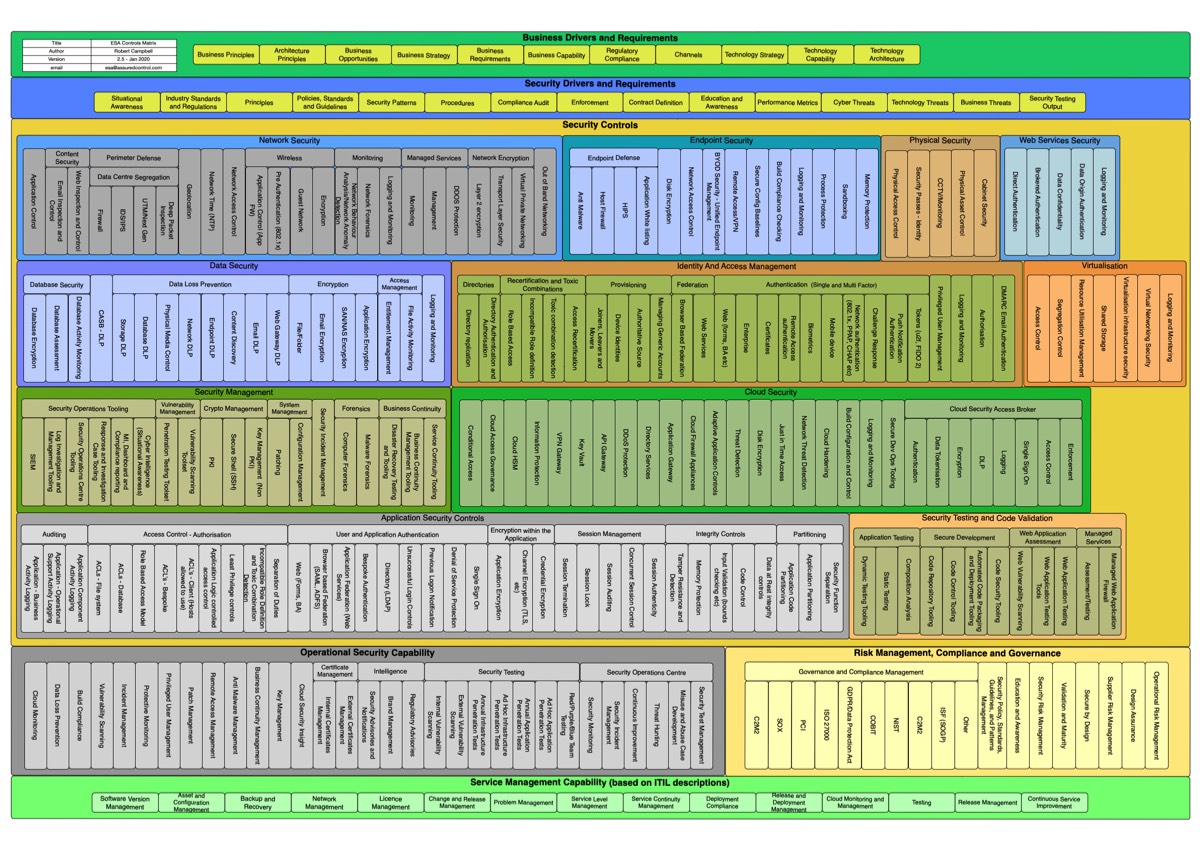
Continue reading “Enterprise Security Architecture To-Be”
Data Poisoning AI Decisions
Rising threat and forecast for 2023 is claimed to be data poisoning, which interestingly enough will impact «AI» -based decisions. AI is still just machine-learning making shit out, on shit in…
AI Artwork – Generators
There are many AI artwork generators out there. The methods vary, but I find those “text to image” quite fun. Check the methods and a selection of tools presented by Nightcafe, create one yourself.
Continue reading “AI Artwork – Generators”Pyramid of Pain, for Crisp Communication
Communicating cyber security will forever be challenging, so whatever tools I find making this easier I like to share. The “good old” Pyramid of Pain (SANS) may be useful to illustrate the complexity of detecting different types of malicious activities, as it is based on typical indicators you might use to detect. I know it does not cover all, but it speaks well. Read the paper yourself and make up your mind.

All the Software Cheat Sheets You Like
With over 5k cheat sheets Cheatography I think covers the most common ones for software development and coding especially.
Cloud Pain Points
A brief but nice summary of pain points we have all experienced?
- Insufficient staff skills
- Data loss/leakage
- API vulnerabilities
- Malware infections
- Insufficient identity and access management controls
- Lack of visibility into what data and workloads are within cloud applications
- Inability to monitor data in transit to and from cloud applications
- Cloud applications being provisioned outside of IT visibility (e.g., shadow IT)
- Inability to prevent malicious insider theft or misuse of data
- Advanced threats and attacks against the cloud application provider
- Inability to assess the security of the cloud application provider’s operations
- Vendors failing to alert customers of vulnerabilities
- Inability to maintain regulatory compliance
- Misconfigurations of cloud hardware and/or cloud software
By Threatpost
Threat Modeling FTW
It is not breaking news, but «amen», Archie!
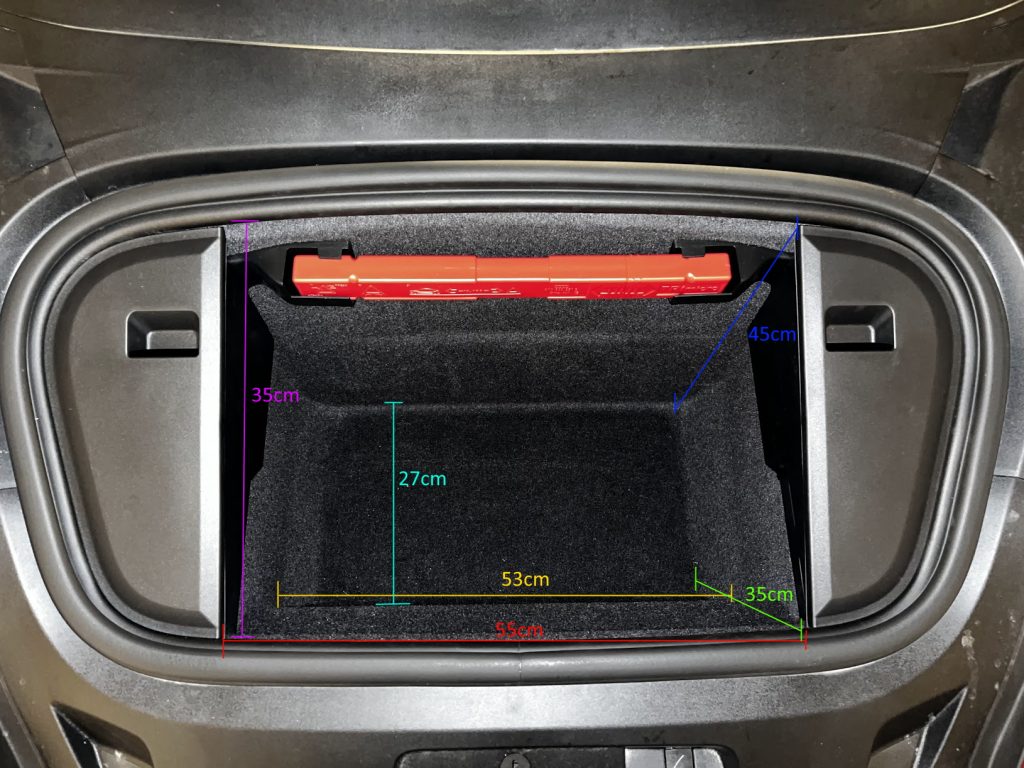
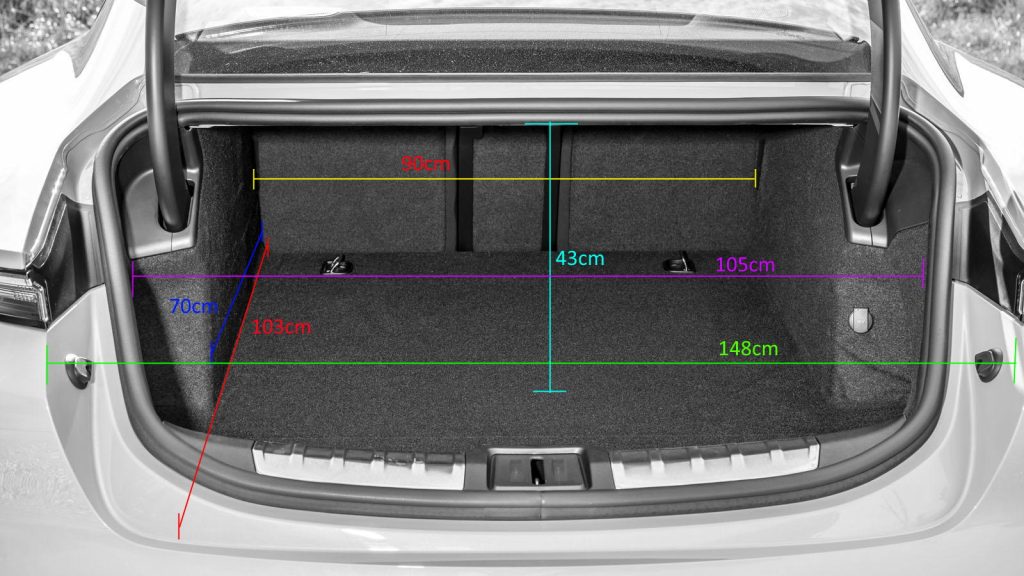
Porsche Taycan Trunk/Frunk Dimentions
Practical and impractical prints
Prusa has made a thingiverse competitor(?), https://www.printables.com/