A selection of historic posts are shown for reference and no new posts will be added to this page.
By the way, most external links in the posts are broken.

Sharing is caring, or whatever…
A selection of historic posts are shown for reference and no new posts will be added to this page.
By the way, most external links in the posts are broken.
May be basic for most cyber Security professionals, but still, several of these cyber documentaries are worth watching while commuting to work or when flying!
I have and will always love the challenge of defining cyber security architecture as a practice, process, lifestyle or what about system security architecture.. you know where I am going. So, there is no “cover it all” definition in my mind, as at least an enterprise security architecture is enterprise dependant and must be – it shall be business driven and therefore not globally defined. However, there are a lot of resources that help to define this.
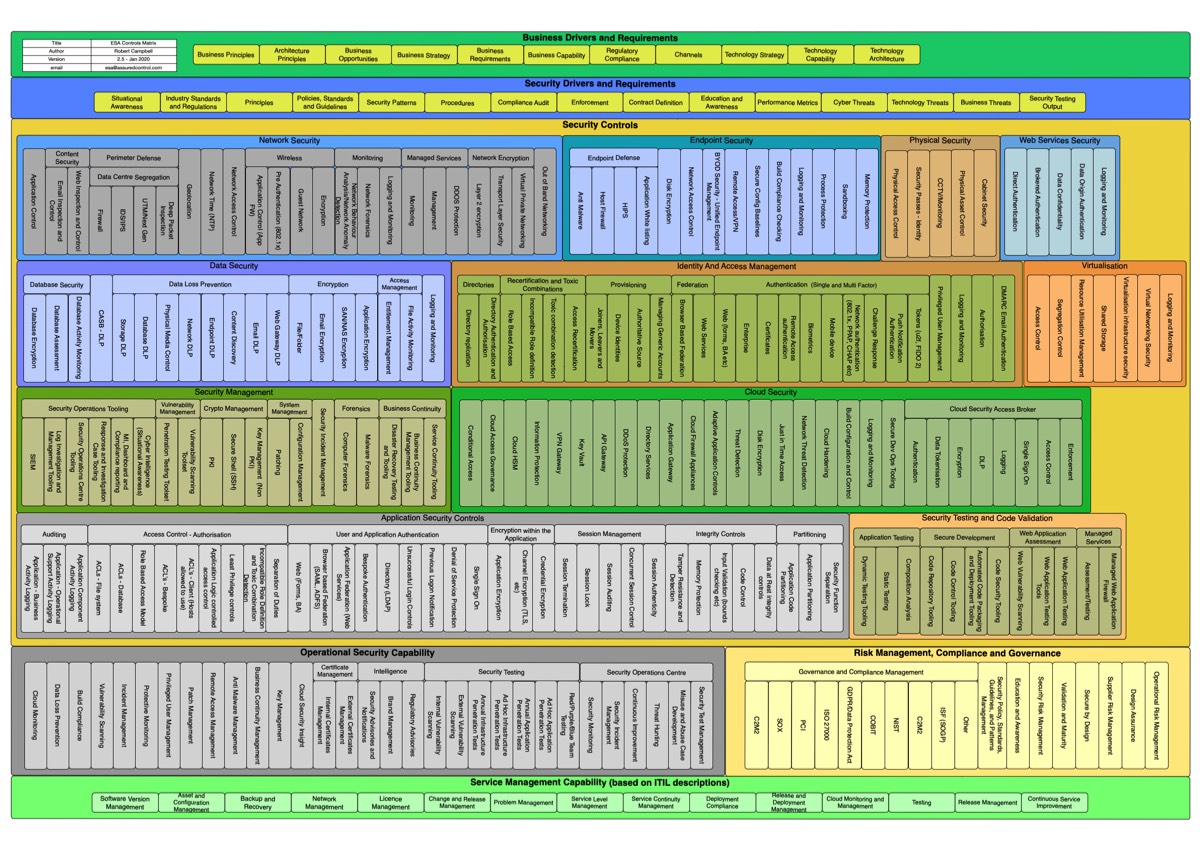
Continue reading “Enterprise Security Architecture To-Be”
Rising threat and forecast for 2023 is claimed to be data poisoning, which interestingly enough will impact «AI» -based decisions. AI is still just machine-learning making shit out, on shit in…
Communicating cyber security will forever be challenging, so whatever tools I find making this easier I like to share. The “good old” Pyramid of Pain (SANS) may be useful to illustrate the complexity of detecting different types of malicious activities, as it is based on typical indicators you might use to detect. I know it does not cover all, but it speaks well. Read the paper yourself and make up your mind.

With over 5k cheat sheets Cheatography I think covers the most common ones for software development and coding especially.
A brief but nice summary of pain points we have all experienced?
By Threatpost
It is not breaking news, but «amen», Archie!
Prusa has made a thingiverse competitor(?), https://www.printables.com/
«The cloud-native ecosystem typically has the four C’s of cloud security: cloud, clusters, containers and code. Each layer builds on the next and insecurities at any layer can impact the layers that follow, such as applications deployed on insecure containers.» Csoonline sais.
Scan them with, e.g., Open-source options such as Anchore and Trivvy during or before deployment.