Looked into the Android SpySMS torjan as they say it has infected 40k users phones. This Mobile Trojan is using SMS as C&C protocol the way IRC C&C were used by PC Trojans back in the days. Got me thinking that the reliable SMS protocol is a nice protocol to control the android bots. The way this app try to block anti-virus from running and the long list of banking apps it controls is rather interesting as this has historically been more adapted by PC trojans and malware.
Facebook Security Education for Dummies
They do so by providing a Capture The Flag “hacking” challenge environment, open source (at Github) for everyone to play with. Might give it a go one time.
How not to do Information Security
 Nice blog post from Lenny Zeltser about mistakes to avoid working with Information Security. Most are probably obvious for many of you, but still… How many do just “Ban the use of external USB drives while not restricting outbound access to the Internet”? 🙂
Nice blog post from Lenny Zeltser about mistakes to avoid working with Information Security. Most are probably obvious for many of you, but still… How many do just “Ban the use of external USB drives while not restricting outbound access to the Internet”? 🙂
Simple file recovery
 Have been out travelling in south america, and guess what. Corrupted camera memory cards are rather common. Used the simple recovery tool Recuva from Piriform to crawl a friends photos and videos from a corrupted and later formatted memory card. Worked perfectly and best of all it has a great user interface, compared to all those command line forensic toolkits such as Skalpel and Foremost.
Have been out travelling in south america, and guess what. Corrupted camera memory cards are rather common. Used the simple recovery tool Recuva from Piriform to crawl a friends photos and videos from a corrupted and later formatted memory card. Worked perfectly and best of all it has a great user interface, compared to all those command line forensic toolkits such as Skalpel and Foremost.
Check it out here
Cybersecurity for Dummies, for free!
 If you like to learn more about cyber security, cyber warfare, advanced persisten threats and more, this is actually worth reading. Dont expect expert insight, but it is a starting point for those who like to get involved with one of the most interesting challenges of todays digitalized society. And it’s provided by Palo Alto for free here!
If you like to learn more about cyber security, cyber warfare, advanced persisten threats and more, this is actually worth reading. Dont expect expert insight, but it is a starting point for those who like to get involved with one of the most interesting challenges of todays digitalized society. And it’s provided by Palo Alto for free here!
Wish I was hit by a ransomwhere
 After reading about Kaspersky having solved the CoinVault ransomwhere campaign, it would have been awesome to test how the decryption application actually works.
After reading about Kaspersky having solved the CoinVault ransomwhere campaign, it would have been awesome to test how the decryption application actually works.
For those of you who are affected by CoinVault, check out the tool here.
Now there is a also a tool for TeslaCrypt by CISCO.
Less than 1% of Android devices had a PHA installed in 2014
According to Google, by October 2014 less than 0,5% of Android devices had Potentially Harmful Application (PHA) installed. That number is excluding non-malicious Rooting apps, but that is no surprise.
And, more importantly, “fewer than 0.15% of devices that download only from Google Play had a PHA installed.”
One main reason was that Google made improvements in the Android platform security technology, e.g., using SELinux sandboxing and use of Verify Apps functionality.
Read the full article here.
App reenginering – simplified
 With a keen interest in information security, mobile technology, and digital forensics I have done quite a bit of mobile app security analysis for fun. 100 000 new apps are released in app-stores every day and some claim there is a significant number of malicious apps among them. I don’t disagree, based on the analyses I have done. Continue reading “App reenginering – simplified”
With a keen interest in information security, mobile technology, and digital forensics I have done quite a bit of mobile app security analysis for fun. 100 000 new apps are released in app-stores every day and some claim there is a significant number of malicious apps among them. I don’t disagree, based on the analyses I have done. Continue reading “App reenginering – simplified”
Fake base stations, surprised?
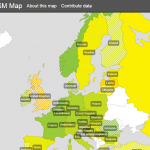 Fake base stations have been identified around government buildings in Oslo, Norway (according to Aftenposten). According to GSM Security Map, which compares the protection capabilities of mobile networks, Norway is ranked above with regards to the adaption of protection mechanisms to GSM networks. Does not seem “above” is enough to withstand fake base stations, unfortunately.
Fake base stations have been identified around government buildings in Oslo, Norway (according to Aftenposten). According to GSM Security Map, which compares the protection capabilities of mobile networks, Norway is ranked above with regards to the adaption of protection mechanisms to GSM networks. Does not seem “above” is enough to withstand fake base stations, unfortunately.
However, the use of fake base stations, even in Oslo, should not be a surprise. In November US marshalls were deploying fake cell towers on airplanes.
Suspicious shortened URLs?
Suspicious about a bit.ly(something) and don’t want to open it? Unshort.me let you check the origin of whatever shortened URL you receive in chat rooms, web-sites, email etc.
