Designed and printed this Raspberry Pi and 5″ LCD touch panel case for my to-be portable security box. Keywords: Kali, Forensics, mobile, whitehat, stealth

Sharing is caring, or whatever…
General posts, not suited elsewhere.

Designed and printed this Raspberry Pi and 5″ LCD touch panel case for my to-be portable security box. Keywords: Kali, Forensics, mobile, whitehat, stealth
Last year we published the Digital Forensics book, after a long and exciting, but challenging, period of work. Together with a team of security and forensics professionals we joined forces to create this “complete” book of Digital Forensics. I had the pleasure to write about the forensics process, based on past digital forensics research and practice as a technical analyst. The book aim to provide practitioners of computer science, information security and law enforcements with a fundamental understanding of digital forensics.
Please see our latest blog post for the first chapter of the book here. The book can be found at Wiley or you can buy it straight from Amazon.
Introduction tutorials for binching?
 www.nomoreransom.org to be tested when…, ehm if….
www.nomoreransom.org to be tested when…, ehm if….
CSO Online makes trivial cyber security heads-up videos, and some are quite Nice actually.
A new version of CSF is out with a few changes [NIST and csoonline]:
Ways to request access or recover data from a platform, identity and access service or social media. The best you can do is to prepare for it to be lost, establish recovery e-mail, sms, friends/family members recovery accounts etc.
They say it will be discontinued in April. It’s rather sad, liked the initiative and how it made it simple to the ordinary IT user to update apps. Look for SUMo (Software Update Monitor), uCheck and more here for a replacement.
Portscanning done “silently” using powershell does not require administrative privileges, thus being a tool where nmap (or similar tools) is no option (due to time and/or authorisation constraints).
The PSnmap tool utilise Powershell capabilities in its module for port scanning.
Install-Module -Name PSnmap -Scope CurrentUser
Get-Module -ListAvailable
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Scope CurrentUser
Import-Module -Name PSnmap
PSnmap -Cn 192.168.1.1 -ThrottleLimit 5 -Timeout 5 -PortConnectTimeoutMs 5 -Verbose > test.txt
To scan more stealth, adjust throttle limit (HIDS may detect resource intensive processes), and timeout values. See full list here.
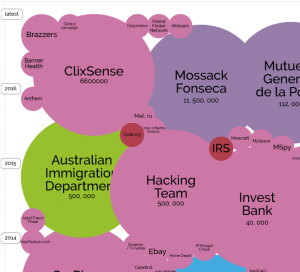 Information is Beautifull still propagate their “World’s Biggest Data Breaches” map. A great way to show why cyber security is important in means of both protection and detection. The worst are probably not even in this map…
Information is Beautifull still propagate their “World’s Biggest Data Breaches” map. A great way to show why cyber security is important in means of both protection and detection. The worst are probably not even in this map…