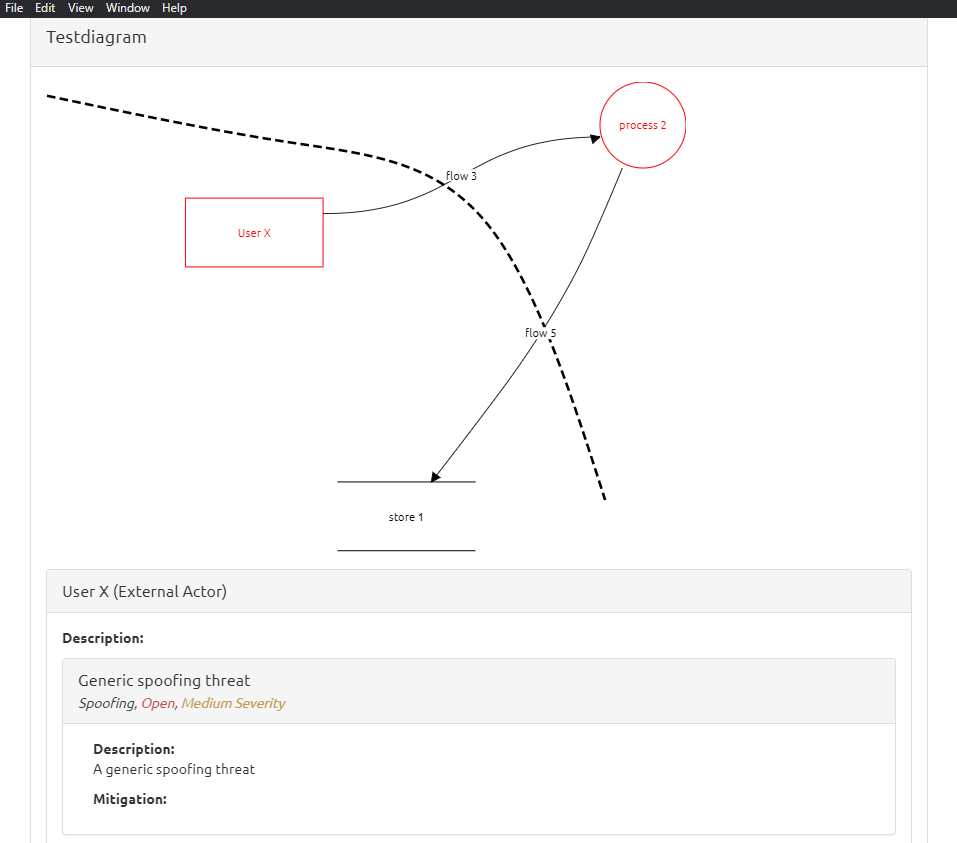
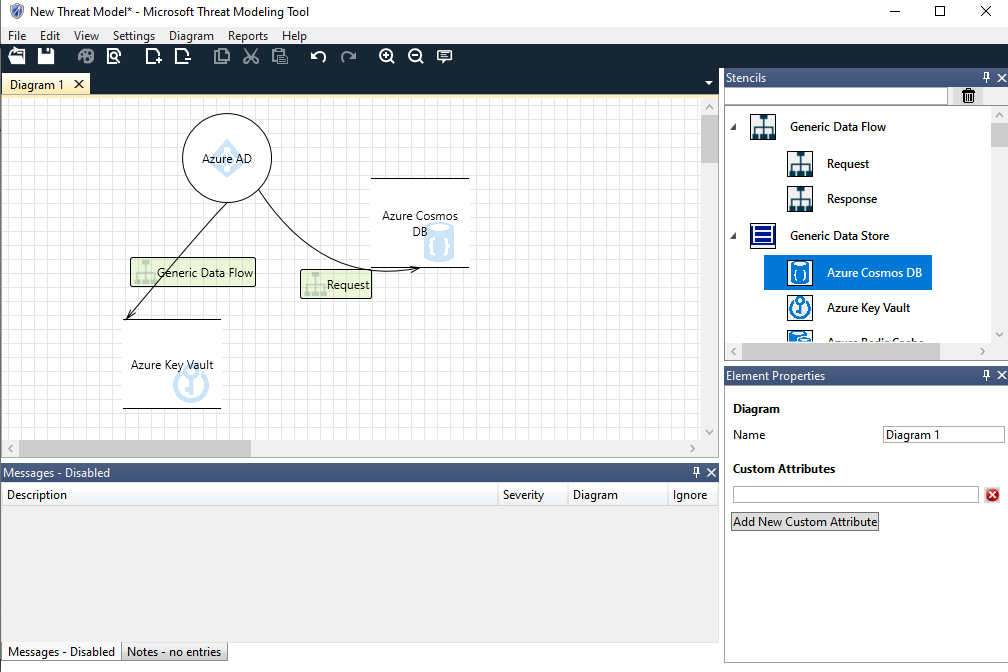
«The cloud-native ecosystem typically has the four C’s of cloud security: cloud, clusters, containers and code. Each layer builds on the next and insecurities at any layer can impact the layers that follow, such as applications deployed on insecure containers.» Csoonline sais.
Scan them with, e.g., Open-source options such as Anchore and Trivvy during or before deployment.