Just got my hands on a “broken” Macbook Pro. It seemed to be a bug with the installed hard drive. So in order to verify this I inserted an old hard drive I had laying around. It turned out to have Windows 8 installed from the last time I was playing around with it on my old (7 years) FujitsuSiemens.
 Guess what happened when I booted the Mac. The MS Windows logo appeared, telling me it was preparing components. And after two minutes, Windows was running smooth on this old Macbook Pro. That’s what I call plug’n’play
Guess what happened when I booted the Mac. The MS Windows logo appeared, telling me it was preparing components. And after two minutes, Windows was running smooth on this old Macbook Pro. That’s what I call plug’n’play

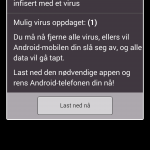
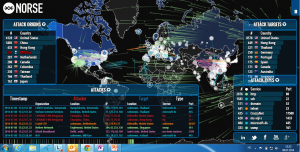 Norse has made an
Norse has made an  It is now 7 years since we did this bachelor thesis project, and it is nice to see the
It is now 7 years since we did this bachelor thesis project, and it is nice to see the 



