 Just diasembled this broken Xperia Z1 with a New lcd display. The module based architecture of this peace made it simple. Keep in mindre that you break the guaranty and that the glue might hve to be replaced if you are too eager disasembling it. Continue reading “Xperia Z1 broken screen easy fixed”
Just diasembled this broken Xperia Z1 with a New lcd display. The module based architecture of this peace made it simple. Keep in mindre that you break the guaranty and that the glue might hve to be replaced if you are too eager disasembling it. Continue reading “Xperia Z1 broken screen easy fixed”
Cybersecurity for Dummies, for free!
 If you like to learn more about cyber security, cyber warfare, advanced persisten threats and more, this is actually worth reading. Dont expect expert insight, but it is a starting point for those who like to get involved with one of the most interesting challenges of todays digitalized society. And it’s provided by Palo Alto for free here!
If you like to learn more about cyber security, cyber warfare, advanced persisten threats and more, this is actually worth reading. Dont expect expert insight, but it is a starting point for those who like to get involved with one of the most interesting challenges of todays digitalized society. And it’s provided by Palo Alto for free here!
Wish I was hit by a ransomwhere
 After reading about Kaspersky having solved the CoinVault ransomwhere campaign, it would have been awesome to test how the decryption application actually works.
After reading about Kaspersky having solved the CoinVault ransomwhere campaign, it would have been awesome to test how the decryption application actually works.
For those of you who are affected by CoinVault, check out the tool here.
Now there is a also a tool for TeslaCrypt by CISCO.
Less than 1% of Android devices had a PHA installed in 2014
According to Google, by October 2014 less than 0,5% of Android devices had Potentially Harmful Application (PHA) installed. That number is excluding non-malicious Rooting apps, but that is no surprise.
And, more importantly, “fewer than 0.15% of devices that download only from Google Play had a PHA installed.”
One main reason was that Google made improvements in the Android platform security technology, e.g., using SELinux sandboxing and use of Verify Apps functionality.
Read the full article here.
App reenginering – simplified
 With a keen interest in information security, mobile technology, and digital forensics I have done quite a bit of mobile app security analysis for fun. 100 000 new apps are released in app-stores every day and some claim there is a significant number of malicious apps among them. I don’t disagree, based on the analyses I have done. Continue reading “App reenginering – simplified”
With a keen interest in information security, mobile technology, and digital forensics I have done quite a bit of mobile app security analysis for fun. 100 000 new apps are released in app-stores every day and some claim there is a significant number of malicious apps among them. I don’t disagree, based on the analyses I have done. Continue reading “App reenginering – simplified”
Cheap Virtual Reality (VR) of your adventures
 Just bought a pair of coolboard from ebay. Its made out of papp and it is and feels cheap. However I found it quite cool. Not Just becase it lets you to have a VR rollercoaster experience, or can fly in google earth. You can also use it for your own 360* photospheres. Let’s say you want to show a few friends how awesome time you had skiing this weekend. Make sure to take the whole 360* photosphere using google camera for Android, use the Coolboard app from Google to show it, then put your handset into the coolboard and show them the real VR ski-trip experience!
Just bought a pair of coolboard from ebay. Its made out of papp and it is and feels cheap. However I found it quite cool. Not Just becase it lets you to have a VR rollercoaster experience, or can fly in google earth. You can also use it for your own 360* photospheres. Let’s say you want to show a few friends how awesome time you had skiing this weekend. Make sure to take the whole 360* photosphere using google camera for Android, use the Coolboard app from Google to show it, then put your handset into the coolboard and show them the real VR ski-trip experience!
Continue reading “Cheap Virtual Reality (VR) of your adventures”
Clone and extend your SSD
 SSD disk sizes have increased significantly over the last years, and the prices for 128GB and up are now getting cheaper.
SSD disk sizes have increased significantly over the last years, and the prices for 128GB and up are now getting cheaper.
I wanted to replace my old 128GB with at new larger and did not want to re-install the OS. Continue reading “Clone and extend your SSD”
Games Time Machine
 Archive.org is more than a time machine for web sites. They now offer games as well. My favorites are Prince of Persia, Doom, Wolfenstein 3D to mention some.
Archive.org is more than a time machine for web sites. They now offer games as well. My favorites are Prince of Persia, Doom, Wolfenstein 3D to mention some.
Try them out here!
Tor’s problem; Traffic Correlation Attacks
 In the need for privacy (with bad or good intentions), people search for tools that can provide anonymous communication online. Tor is well known for that and have existed for a long time as a respected network of multiple layers of hops and encryption (“onion rings”). Just found this interesting article from Aaron M. Johnson et.al. where they have exploited vulnerabilities in Tor network by using traffic correlation attacks. Continue reading “Tor’s problem; Traffic Correlation Attacks”
In the need for privacy (with bad or good intentions), people search for tools that can provide anonymous communication online. Tor is well known for that and have existed for a long time as a respected network of multiple layers of hops and encryption (“onion rings”). Just found this interesting article from Aaron M. Johnson et.al. where they have exploited vulnerabilities in Tor network by using traffic correlation attacks. Continue reading “Tor’s problem; Traffic Correlation Attacks”
Fake base stations, surprised?
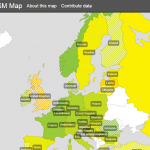 Fake base stations have been identified around government buildings in Oslo, Norway (according to Aftenposten). According to GSM Security Map, which compares the protection capabilities of mobile networks, Norway is ranked above with regards to the adaption of protection mechanisms to GSM networks. Does not seem “above” is enough to withstand fake base stations, unfortunately.
Fake base stations have been identified around government buildings in Oslo, Norway (according to Aftenposten). According to GSM Security Map, which compares the protection capabilities of mobile networks, Norway is ranked above with regards to the adaption of protection mechanisms to GSM networks. Does not seem “above” is enough to withstand fake base stations, unfortunately.
However, the use of fake base stations, even in Oslo, should not be a surprise. In November US marshalls were deploying fake cell towers on airplanes.
